We spoke to Chern-Yue Boey, Senior Vice President, Asia-Pacific, SailPoint recently and asked him – why should anyone besides IT managers care about identity and access management (IAM)? Besides an expected CAGR of 15.5% globally with projected market size of USD 32.6 billion by 2028, Boey also pointed out key opportunities that Asia Pacific organizations need to address both from user and provider perspectives.
According to Market and Markets, the global IAM market growth trajectory is largely attributed to demands stemming from increased cybersecurity risks, such as enterprise security breaches, mismanagement of data, and “escalating instances of identity-related fraud”. Another contributing factor is the rapid adoption of AL/ML-powered services that can help organizations more effectively scale, enhance and manage identity and access management.

“Digital transformation accelerated at a breakneck speed during the pandemic,” said Boey.
So why were organizations forced to ramp up to a secure, scalable, yet manageable enterprise identity management strategy? Boey noted increased vulnerabilities was not only due to employees accessing potentially secure information from less-than-ideal home based networks, but also a surge of additional data when customers moved more personal data and secure transactions fully online within the span of weeks during the pandemic.
Many would think that organizations may have learned a few lessons in enterprise IAM from these past scenarios, however, SailPoint’s Horizon of Identity Security Report found that 45% of the 300 enterprises surveyed still had fragmented identity experiences across their organizations.
Why Do We Need to Care About Identity and Access Management?
With more secure transactions moving online, every person, whether in a professional or personal capacity, will require a fully-secure digital identity to enable seamless collaboration with business partners, and to engage in services (perhaps with banks or public services) while complying fully with security and privacy regulations.
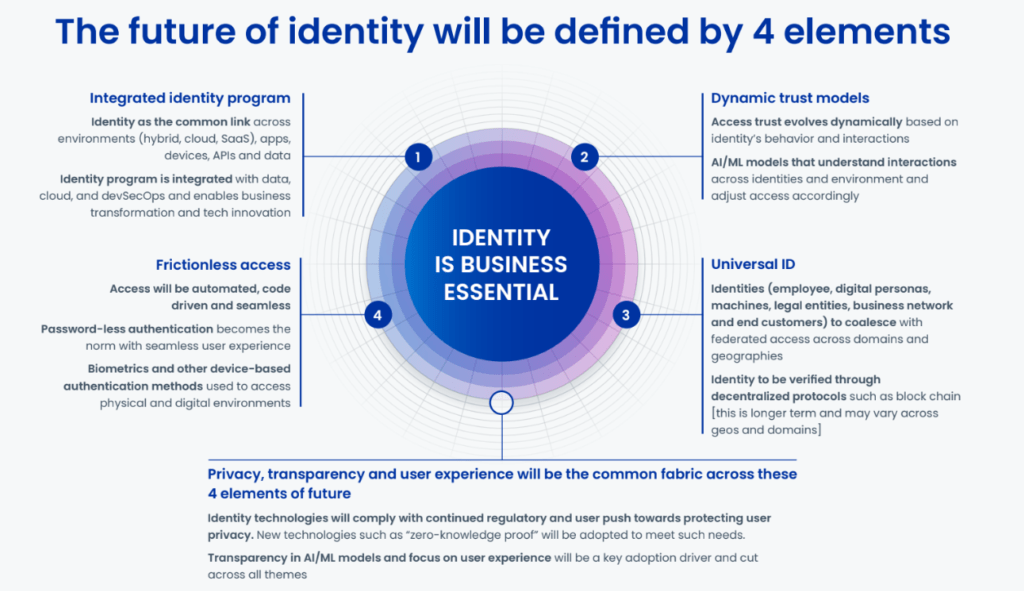
This is no easy feat. As Boey explains, identity and access management in a modern architecture must possess several characteristics to be successful. Firstly, the solution must be digitalized and automated, secondly to be able to provide intelligence to users, and thirdly to allow integration into every digital context within the environment in an extensive and compliant way.
These characteristics echo the shift towards a fully digital customer-engagement environment, where universal identities can be used for frictionless and safe access to services and products, and where dynamic trust models evolve according to user behaviors and interactions.
How AI Contextualizes IAM for Tangible Business Benefits
Speaking to user experience, Boey highlighted the challenges faced by new employees, such as the time-consuming process of obtaining access and setting up a dedicated laptop. The integration of an identity security platform is proposed as a solution to streamline these onboarding procedures, making them more efficient, faster, and ultimately enhancing the overall employee experience.
The importance of provisioning and deprovisioning, including aspects like password reset, is underscored as crucial elements of user experience management.
From a managerial perspective, Boey delves into the retrospective nature of user experience, particularly in the context of access certification processes within organizations. Traditional manual certification processes, prone to rubber stamping and potential inaccuracies, are contrasted with modern AI-based security enterprises.
Boey outlines how AI and a patented algorithm contribute to a more proactive approach by identifying outliers in access certifications. This shift enables managers to focus on meaningful decision-making rather than merely rubber-stamping approvals, fostering a more robust and accurate security environment
Additionally, with the use of generative AI, specifically in using Large Language models (LLM), LLMs can assist users in understanding technical descriptions, making the approval process more accessible and transparent.
AI also has the potential to improve the auditing process, where AI-driven solutions can automate and provide ongoing dynamic assessments, enabling Chief Information Security Officers (CISOs) to offer real-time insights into the security environment. This not only reduces the effort required for periodic audits but also enhances the overall security posture of the organization.
Adopting a Robust IAM Needs a Top-Down, “Worst-Case” Approach
The CISO must drive the understanding throughout organizations that “you need to assume that you will be breached,” said Boey. A strong identity and access management (IAM) program not only boosts security, it can also reduce costs associated with security operations, improve operational efficiency, and speed attack response and recovery.
Organizations must move away from a “reactive” security culture, acknowledge the complexities in managing digital identities, and accelerate their execution of extended and unified identity management strategies.







